De très nombreux exemples de phrases traduites contenant "there is a protocol" – Dictionnaire françaisanglais et moteur de recherche de traductions françaises Le protocole ISIS fait l'objet d'une spécification détaillée dans la norme ISO/IEC 105 Il définit un protocole de routage de type intradomaine pour les réseaux de type CLNP dont les principes sont décrits dans les normes ISO/IEC 8473 à Son adaptation au protocole IP fait de lui un IGP de type Link State comparable au protocole OSPFIntroduction ISIS, or Intermediate System to Intermediate System, is an open standard routing protocol ISO published the standard as a way to route datagrams as part of their OSI stack IETF later republished the standard, and added IP route support There are a lot of similarities between ISIS and OSPF
Introduction To Is Is Network Direction
Is is protocol administrative distance
Is is protocol administrative distance-Scribd es red social de lectura y publicación más importante del mundoThe Protocol IT services (Protocol IT IS Services Pty Ltd) is a Canning Vale, South of the river Perth, Western Australian based company that strives to provide results orientated consultancy that delivers innovative technologybased solutions to manage your business and corporate IT needs With over years of industrial excellence Protocol IT, it has expanded its wings to Asia and the




Rip Vs Ospf What Is The Difference Fs Community
Going far beyond the basics of the protocol, Hannes details the many design touchesboth subtle and not so subtlethat go into creating a realworld ISIS implementation This book is a mustread for anyone who wants to understand ISIS at a deep level, from network architects wanting to understand how to design a largescale ISIS network to software engineers wanting to write ISIS Interview Questions – ISIS is a link state routing protocol Commonly used in Service Provider networks Back in old days, ISIS routing protocol software was more stable and robust compare to OSPF, thus many service provider choose ISIS as their interior routing protocol This protocol (which is NOT an updated version of the August 12 DF Protocol) facilitates compliance with the CFTC's rulemakings on (i) Swap Trading Relationship Documentation, Confirmation, Portfolio Reconciliation and Portfolio Compression, (ii) EndUser Exception to the Clearing Requirement and (iii) Clearing Requirement Determination Required
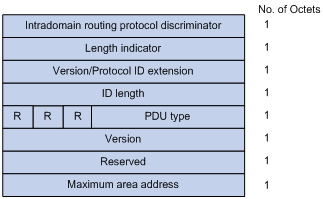
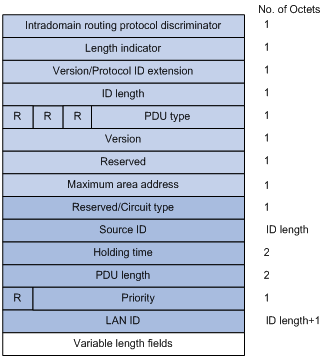
The communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL) Our journey in this article will be a deep dive into the world of HTTP vs HTTPs, and how they work, and I will show you how to make sure your site survives any technical issues when migrating from one protocol to another HereProtocol Extensions for Support of Diffservaware MPLS Traffic Engineering Category Standards Track Defines ISIS subTLV (22, 22) Bandwidth Constraints Defines OSPF subTLV (2, 17) Bandwidth Contraints Defines RSVP class 66 (CLASSTYPE) Management Information Base for Intermediate System to Intermediate System (ISIS)Version/Protocol ID Extension ID Length R R R PDU Type Version Reserved Maximum Area Addresses NSAP Addressing Authentication Plaintext, MD5 Interdomain Part (IDP) Portion of the address used in routing between autonomous systems;
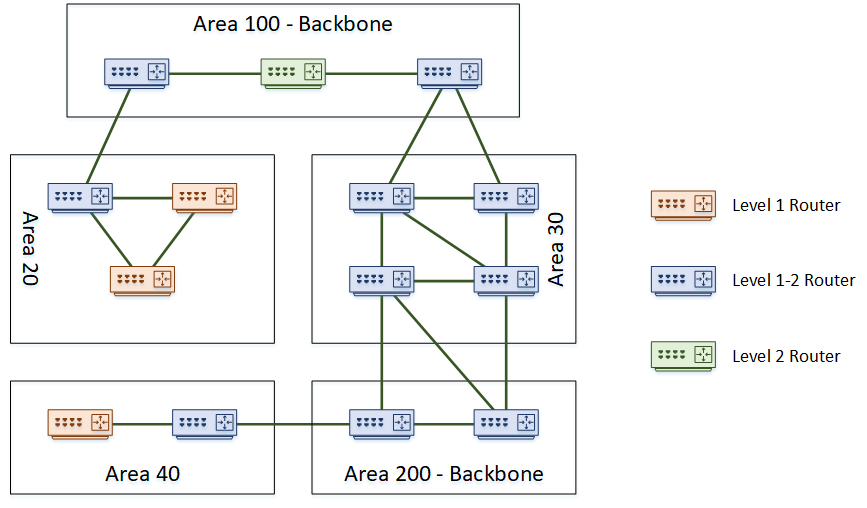
The ISIS protocol is described in detail in ISO Standard 105, the entire contents of which are incorporated herein by reference This ANSI ISIS protocol is used as the interior gateway protocol (IGP) of the NSFNET backbone InterDomain Routing Protocol Information EXTERNAL INFORMATION contains interdomain routing protocol information, and is passed transparently by the ISIS protocolIn this video series I talk about the ISIS protocol ISIS Characteristics Basic ISIS Implementations Advanced ISIS Implementation ISIS Level1 I Le protocole ISIS est aujourd'hui déployé sur un très grand nombre de réseaux dorsaux d'opérateurs Le transport sur des réseaux IP des services Voix et Vidéo (fortes contraintes temps réel) impose certaines adaptations des technologies utilisées dans ces réseaux Cet article détaille le plan d'adressage, le découpage en tâches et les différentes phases utilisées par ISIS Il termine par les spécificités et extensions du protocole ISIS




Is Is Protocol Introduction



Routing Protocol Network Encyclopedia
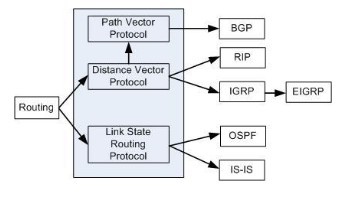
Intermediate System to Intermediate System intradomain routing protocol IS, ES Is a Link State Protocol Is a dynamic routing protocol based on SPF routing algorithm IS is "OSI speak" for router (ie, routing protocol for the ISO Connectionless Network Protocol)ⓘ ISIS est un protocole de routage interne multiprotocoles à états de lien Ce protocole est défini dans la norme internationale ISOCEI de lOpen SystISIS został opracowany przez ISO (The International Organization for Standardization) jako protokół routingu dla CLNP (Connectionless Network Protocol) Wersja ISIS, która wspiera routing IP i CLNP nazywana jest Dual ISIS lub Integrated ISIS ISIS – działanie protokołu Protokół działa w zakresie jednego systemu autonomicznego (AS)



Is Is Adjacency Ipcisco




Basic Integrated Is Is Router Configuration Configuring Is Is Protocol Cisco Press
Le protocole ISIS (Intermediate System to Intermediate System) est un protocole de routage conçu pour déplacer des informations en déterminant le meilleur itinéraire pour les datagrammes via un réseau à commutation de paquetsThe ISIS protocol is an interior gateway protocol (IGP) that uses linkstate information to make routing decisions ISIS is a linkstate IGP that uses the shortestpathfirst (SPF) algorithm to determine routes ISIS evaluates the topology changes and determines whether to perform a full SPF recalculation or a partial route calculation (PRC)Le protocole ISIS (Intermediate System to Intermediate System) est un protocole de routage interne à état de liensLe terme « Intermediate System est la terminologie ISO pour désigner un routeur ISIS est comparable à OSPF car ils utilisent tous deux l'algorithme de Dijkstra, ou Open Shortest Path File, pour calculer les meilleurs chemins à travers un réseau




Is Is Packets Integrated Is Is Routing Protocol Concepts Cisco Press



3
ISIS et OSPF sont deux protocoles de routage a états de lien qui utilisent l'algorithme de Dijkstra pour calculer les meilleurs chemins à travers un réseau, ils sont donc conceptuellementAssigned by ISO DomainSpecific Part (DSP) Portion of the address relevant only within the local AS Authority and Format Identifier (AFI)Protocol layering forms the basis of protocol design It allows the decomposition of single, complex protocols into simpler, cooperating protocols The protocol layers each solve a distinct class of communication problems Together, the layers make up a layering scheme or model



Verifying The Is Is Protocol Is Is User Guide Juniper Networks Techlibrary




Introduction To Is Is Network Direction
Caractérisé par le fait que, parallèlement, on établit et entretient une deuxième session sur la base d'au moins un protocole de radiocommunication mobile (WAP) ou au moyen d'une interface utilisateur de radiocommunication mobile (MS) de telle sorte que la première et la deuxième session sont réunies par une communication interprocessus (IPC) dans un serveur de réseau IP (S) enThe ISIS (Intermediate System Intermediate System) protocol is one of a family of IP Routing protocols, and is an Interior Gateway Protocol (IGP) for the Internet, used to distribute IP routing information throughout a single Autonomous System (AS) in an IP network ISIS is a linkstate routing protocol, which means that the routers exchangePart of the IPv4/IPv6 BGP Workshop, by Philip SmithCheck out our latest webinars and online courses at https//apnicacademy
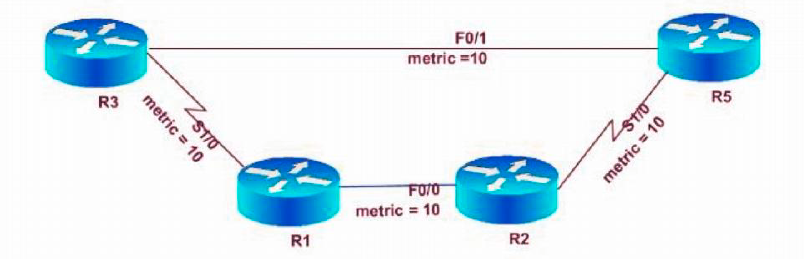



Intermediate System Intermediate System Is Is Protocol Octa Networks




Mpls Basics Mpls Tutorial
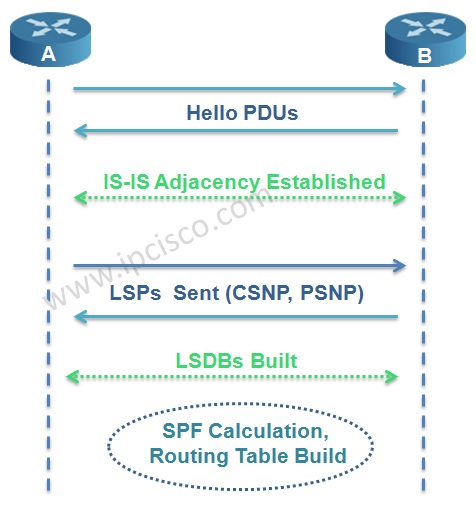
Intermediate SystemtoIntermediate System Protocol (ISIS protocol) is an Interior Gateway Protocol that uses packetswitched networks to support efficient autonomous system routing for Internet service providers and large enterprisesISIS is a linkstate routing protocol, providing fast convergence and excellent scalability Like all linkstate protocols, ISIS is very efficient in its use of network bandwidth Cisco is an active member of the ISIS working group at the IETF, and is responsible for many of the ongoing enhancements to the protocolISIS Network Protocol Basics ISIS is a linkstate interior gateway routing protocol Like OSPF, ISIS runs the Dijkstra shortestpath first (SPF) algorithm to create a database of the network's topology and, from that database, to determine the best (that is, shortest) path to a destination
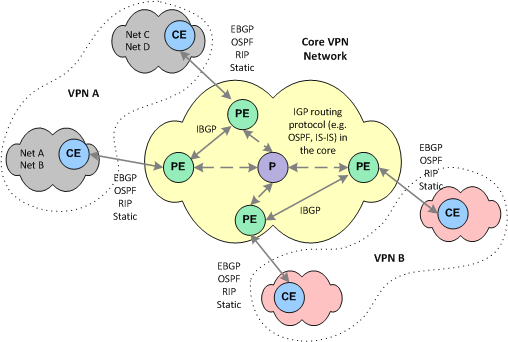



Vpn And Connectivity Services
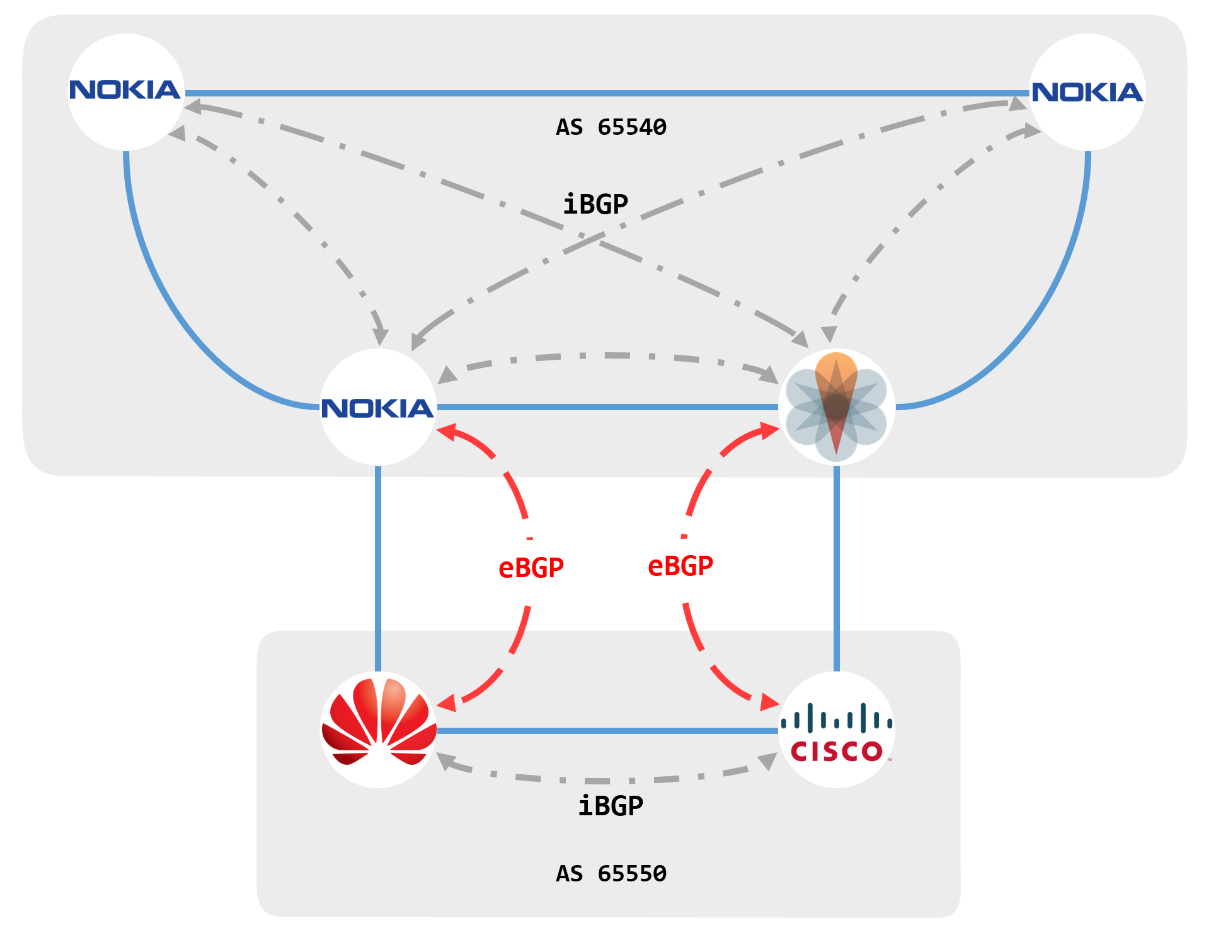



Bgp Configuration In Nokia Cisco Juniper And Huawei Part 1 Routecloud Indonesia Blog
ISIS Protocol uses Dijkstra SPF (Shortest Path First) algorithm like OSPF, to build the ISIS Protocol databases and calculate the best path It uses Cost value at the best path calculation ISIS Protocol is a stable protocol and it has a very fast convergenceIt has also large scalability that ISIS Protocol is a vey good protocol for Service Providers and large enterprises Le protocole II (Intermediate ytem Protocol) et un protocole de paerelle intérieure qui utilie de réeaux à commutation de paquet pour prendre en charge un routage de ytème autonome efficace pour le fournieur de ervice Internet et le grande entreprie II a été défini à l'origine par l'IO / IEC 105 02 par l'Organiation internationale de normaliation et la Commiion Flurry Protocol provides a crosschain token that combines the benefits of a stable coin with uninterrupted yield farming Anyone who wants to get into a DeFi product with lower risk and a much lesser yield farming charge may be interested in this platform
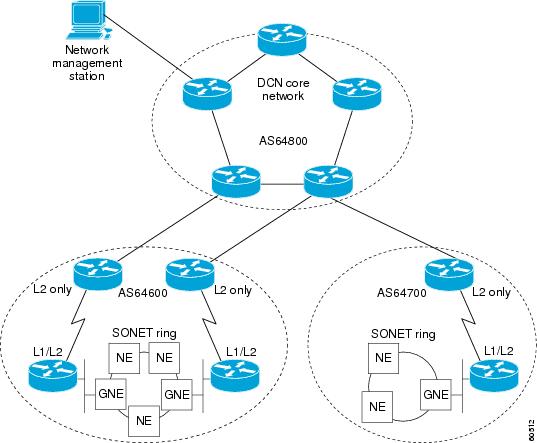



Ip Routing Bgp Configuration Guide Cisco Ios Xe Gibraltar 16 12 X Configuring Multiprotocol Bgp Mp Bgp Support For Clns Cisco Ios Xe 16 Cisco




Introduction To Is Is
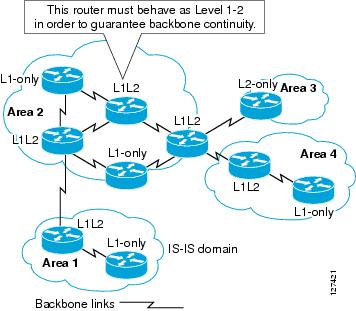
• ISIS is a classless protocol, and thus supports VLSMs Other characteristics of ISIS include • ISIS was originally developed to route the ISO address space, and thus is not limited to IP routing • ISIS routes have an administrative distance is 115 • ISIS uses an arbitrary cost for its metric ISIS additionally has threeISIS est un Interior Gateway Protocol routage à état de liens Comme OSPF, ISIS court le plus court chemin de Dijkstra premier (SPF) algorithme pour créer une base de données de la topologie du réseau et, à partir de cette base de données, pour déterminer le meilleur (à savoir, le plus court) trajet vers une destinationISIS (Intermediate System to Intermediate System Protocol) ist ein LinkState Interior Gateway Protocol (ähnlich OSPF), welches durch die ISONorm 105 spezifiziert ist Ursprünglich ( 1992 ) wurde ISIS für die Verwendung mit dem verbindungslosen Protokoll CLNP entworfen, die Unterstützung für den Einsatz mit IP wurde durch Erweiterungen möglich



Isis Dis Election Labnario




Types Of Routing Protocols 3 1 4 Cisco Networking Academy S Introduction To Routing Dynamically Cisco Press
Protocol has reached out to Passbase, but has yet to hear back We'll update this story if we receive a comment from the company In January, Passbase head of talent, Jenna Bachrouche, posted an article on the company website called, "It's 21 Diversity cannot stay reactive," where she detailed how each of the company's team leaders were going through aThe protocol is called Transport Layer Security (TLS), although formerly it was known as Secure Sockets Layer (SSL) This protocol secures communications by using what's known as an asymmetric public key infrastructure This type of security system uses two different keys to encrypt communications between two parties The private key this key is controlled by the Internet Protocol (IP) est un protocole sans connexion qui, en tant qu'élément central de la famille des protocoles Internet (un ensemble d'environ 500 protocoles réseau), est responsable de l'adressage et de la fragmentation des paquets de données dans les réseaux numériques Avec le protocole de transport TCP (Transmission Control Protocol), l'IP constitue




1 Bgp Protocol Illustration Download Scientific Diagram



Isis Training And Junos Configuration Inetzero Inetzero
ISIS is an IGP, linkstate routing protocol, similar to OSPF It forms neighbor adjacencies, has areas, exchanges linkstate packets, builds a linkstate database and runs the Dijkstra SPF algorithm to find the best path to each destination, which is installed in the routing table ISO has developed standards for two types of routing protocols ESIS discovery protocol —ESIS performs "routing" between End Systems and Intermediate Systems referred as Level 0 "routing" ESIS is analogous to the Address Resolution Protocol (ARP) in IP
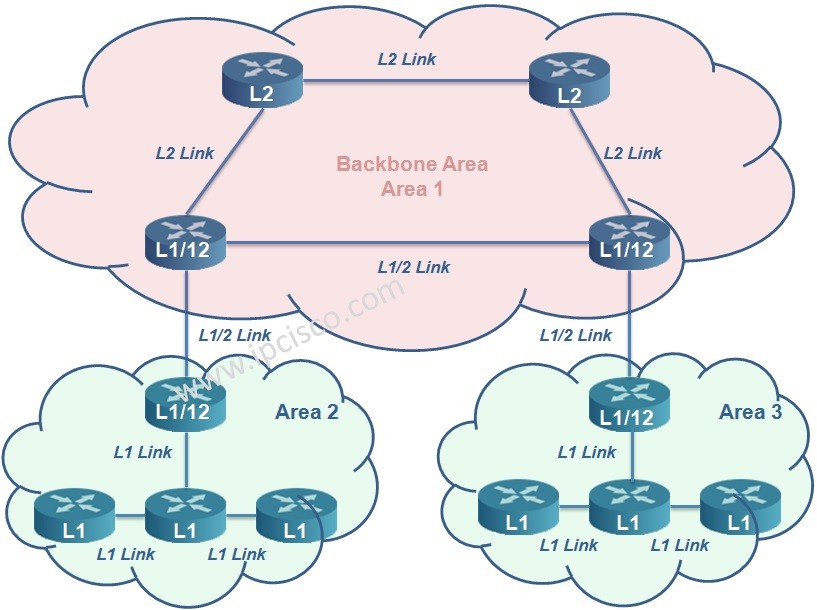



Is Is Ipcisco
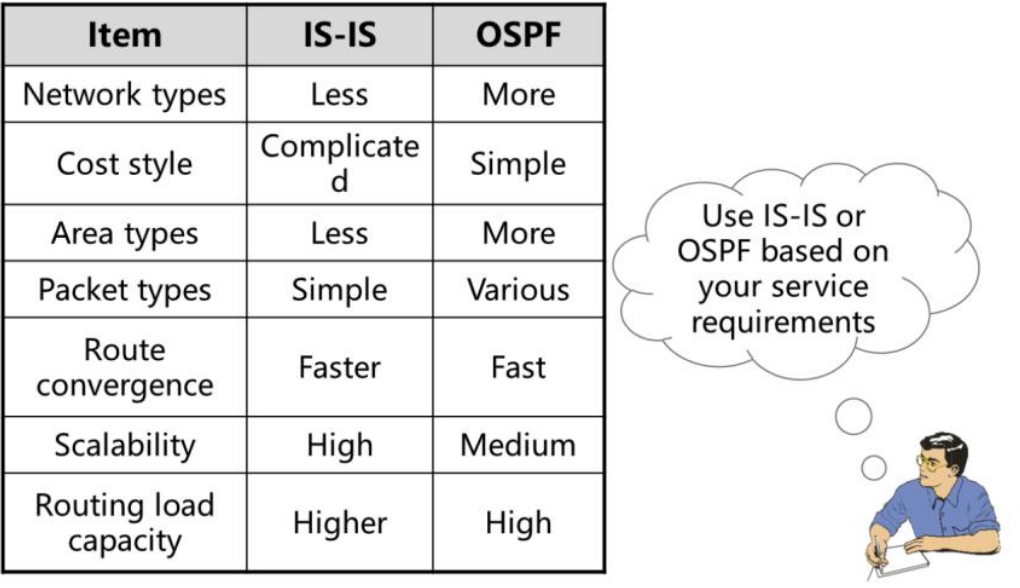



Why Do Many Isps Still Use The Is Is Protocol Instead Of The Ospf Protocol




Rip Vs Ospf What Is The Difference Fs Community
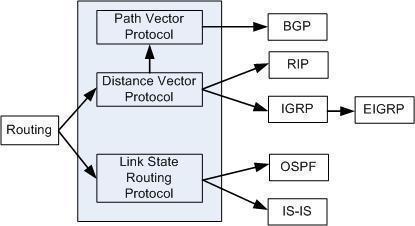



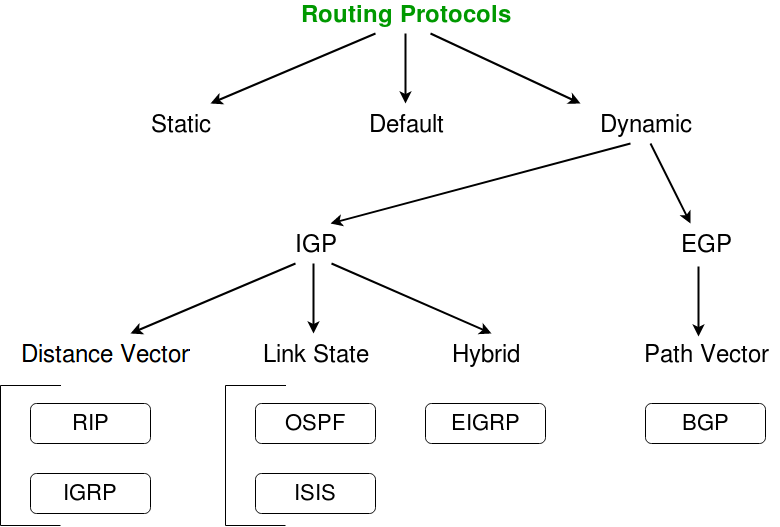
Routing Protocols




Seamless Suffering Routingcraft Net




Introduction To Is Is




Intermediate System To Intermediate System Is Is Routing Protocol Fundamentals Youtube
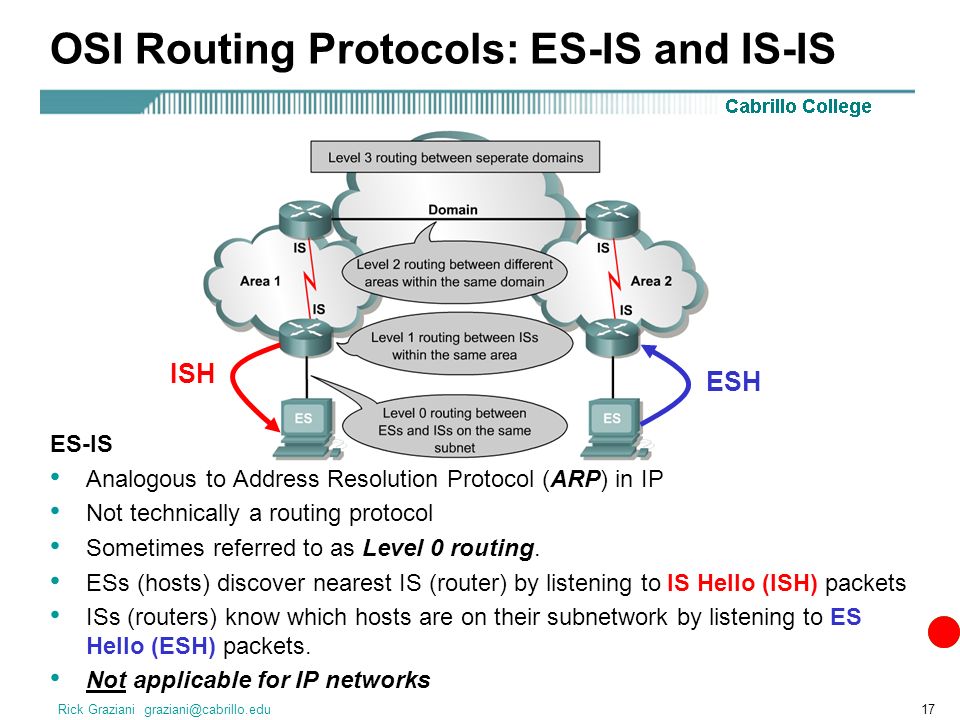



Is Is Intermediate System To Intermediate System Rick Graziani Cabrillo College Fall Ppt Download



1



Foundation Topics Chapter 9 Fundamentals Of The Integrated Is Is Protocol Part Iv Is Is Ccnp Bsci Official Exam Certification Guide Misc Etutorials Org




Is Is Protocol Introduction
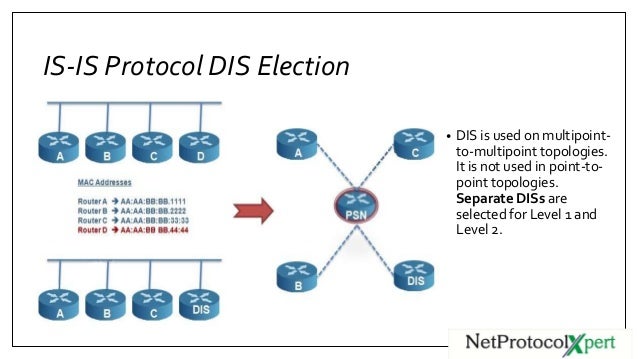



Is Is Protocol Adjacency



What Is Eigrp Fundamentals Benfits Of Eigrp Routing Protocol




Introduction To Is Is
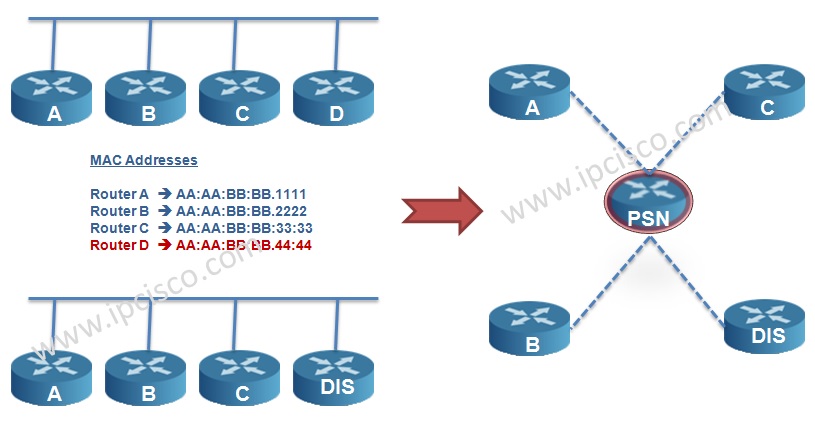



Is Is Adjacency Ipcisco



Why Do Many Isps Still Use The Is Is Protocol Instead Of The Ospf Protocol




Is Is Vs Ospf Differences And Similarities Youtube




Introduction To Is Is




Is Is Terms And Concepts



Isis Training And Junos Configuration Inetzero Inetzero




Dynamic Routing Protocols Explained Icnd1 100 105




The Aerodynamics Of Routing Ciena
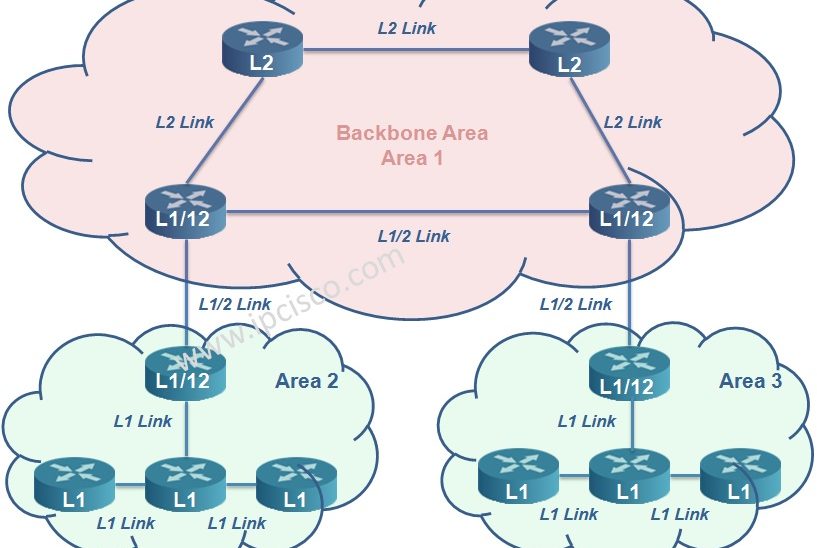



Is Is Protocol Archives Ipcisco




Is Is Hardcore Punk Garage Punk Hardcore Punk
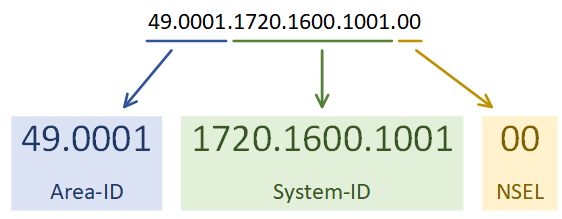



Introduction To Is Is Network Direction



Intermediate System Intermediate System Is Is
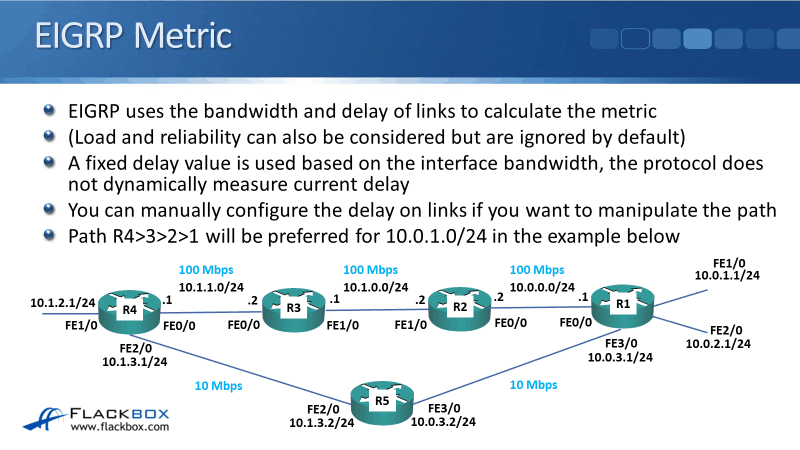



Cisco Routing Protocol Metrics Tutorial Flackbox



Episode 14 Digging Deep Into The Is Is Routing Protocol Network Collective




Pdf Performance Comparison Of Mixed Protocols Based On Eigrp Is Is And Ospf For Real Time Applications




Integrated Is Is Routing Protocol Training With Cisco Ios Advanced 3 Clip1 Youtube
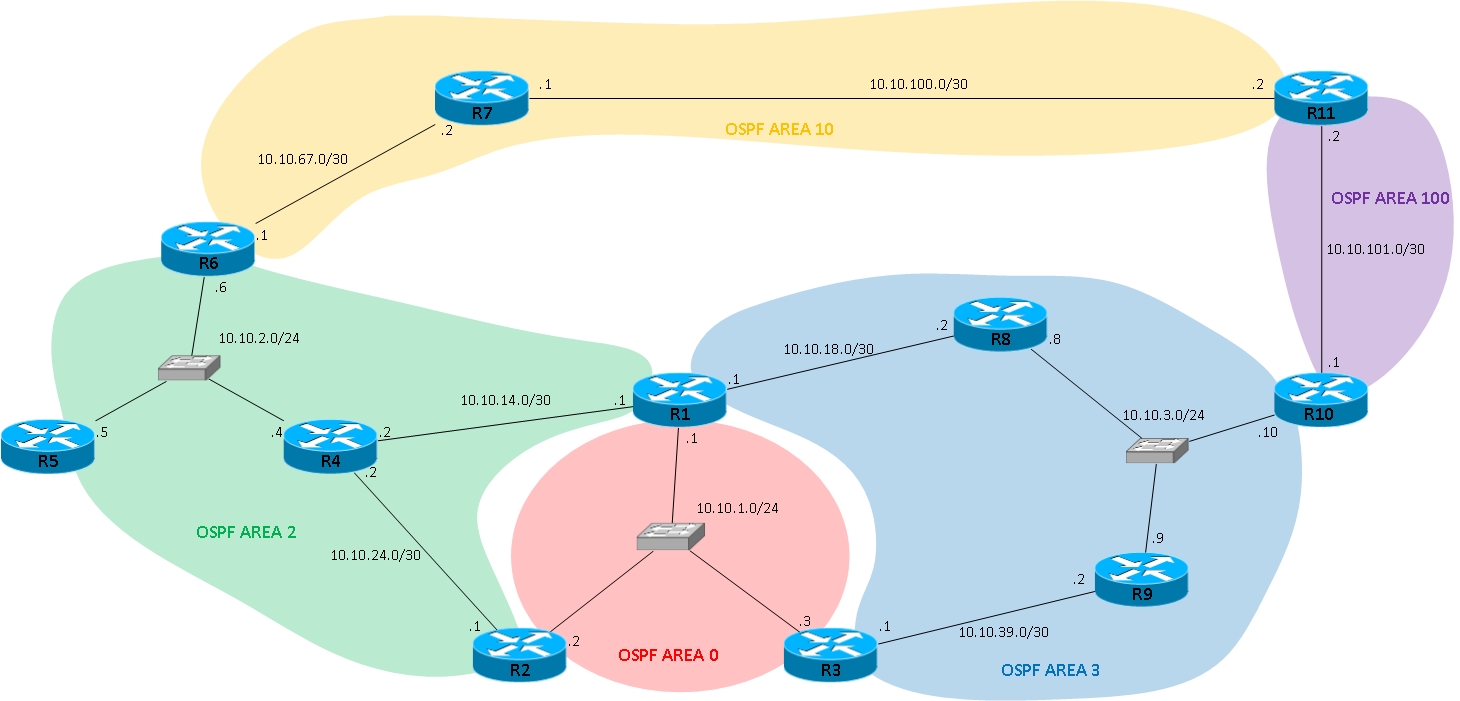



Eigrp Vs Ospf What S The Difference Fs Community




How Many Types Of Routing Protocols By 10 Microsoft Award Mvp Learn In 30sec Wikitechy



Routing V S Routed Protocols In Computer Network Geeksforgeeks



Exterior Gateway Protocols Egp And Bgpv4 Chapter 10 Isp Connectivity With Bgpv4 An Exterior Gateway Path Vector Routing Protocol For Interdomain Routing Integrated Cisco And Unix Network Architectures Networking Etutorials Org



Integrated Is Is Basics Amolak Networks



Www Routeralley Com Guides Isis Pdf




Introduction To Is Is




Is Is Protocol Adjacency




Ospf Vs Isis Detailed Comparison Ip With Ease
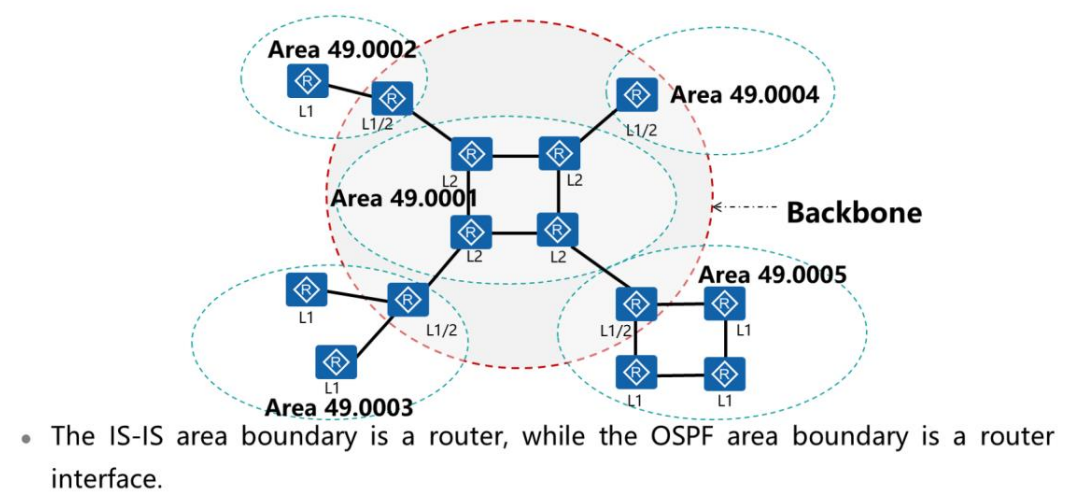



Why Do Many Isps Still Use The Is Is Protocol Instead Of The Ospf Protocol




The Complete Is Is Routing Protocol Computer Science Books Amazon Com
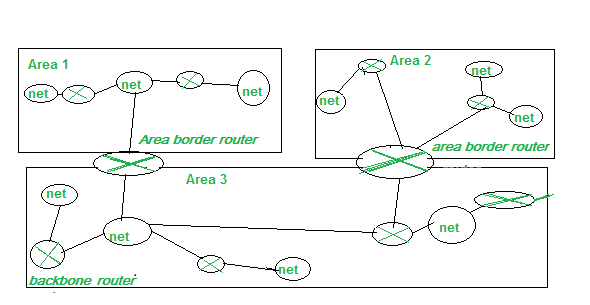



Open Shortest Path First Ospf Set 2 Geeksforgeeks



1



Isis Training And Junos Configuration Inetzero Inetzero




Routing Protocols Wiznet




Example Configuring Backup Selection Policy For Is Is Protocol Technical Documentation Support Juniper Networks
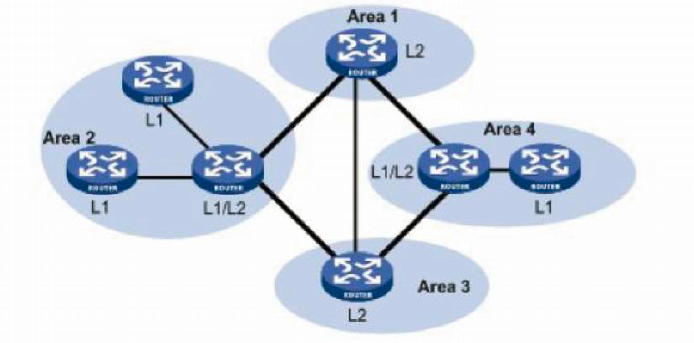



Intermediate System Intermediate System Is Is Protocol Octa Networks



Isis Training And Junos Configuration Inetzero Inetzero



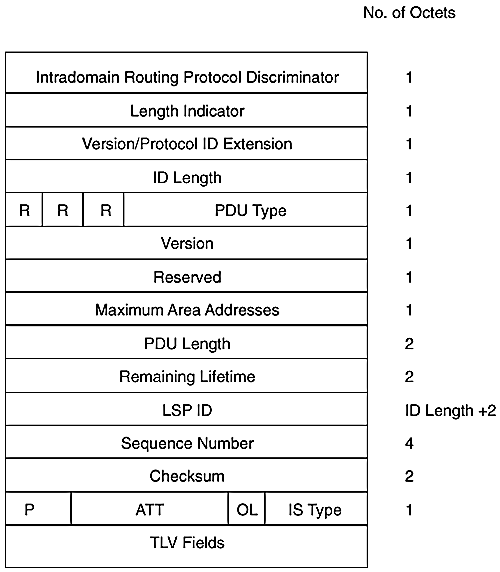
Is Is Pdu Format



Ospf Routing Protocol Dijkstra Algorithm Ospf Stub Area



Is Is Pdu Format



Ip Routing Isis Configuration Guide Is Is Overview And Basic Configuration Cisco Asr 1000 Series Aggregation Services Routers Cisco




Is Is Network Design Solutions Martey Abe Sturgess Scott Amazon Com Books




Isis Cheat Sheet Will Help You On Isis Protocol Network Solution
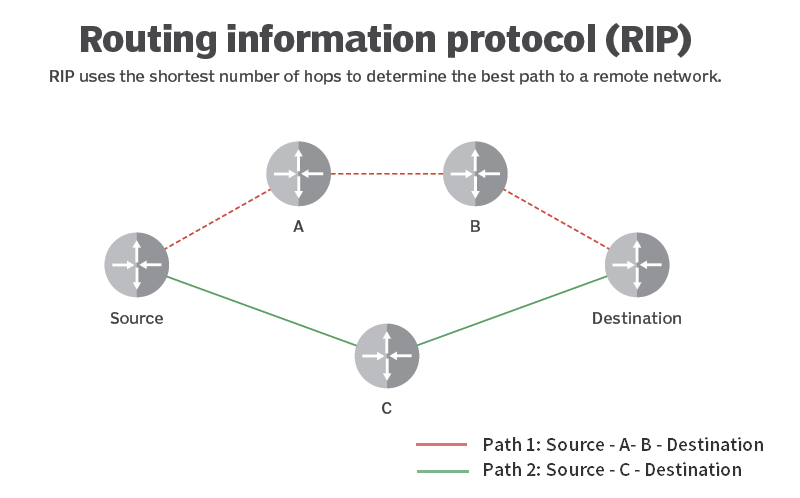



Rip Vs Ospf What Is The Difference Fs Community
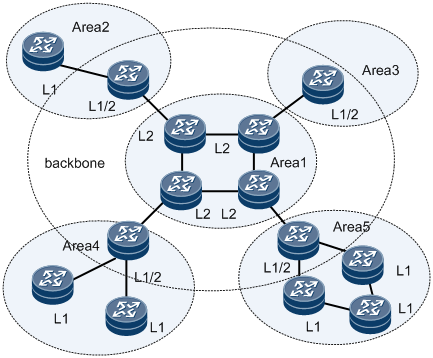



Isis As Sbi Onos Wiki



Www Ijesit Com Volume 4 Issue 2 Ijesit1502 30 Pdf




Isis Narrow And Wide Metrics Mom Network Engineer Juniper Ambassador




Is Is Overview And Lab Ccie




Cisco Routers Integrated Is Is Youtube
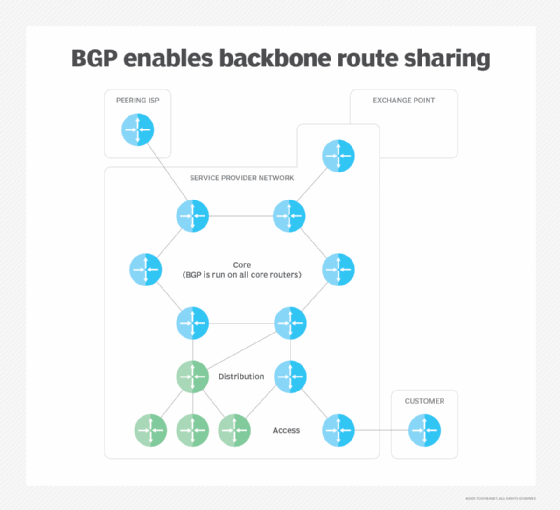



What Is Enhanced Interior Gateway Routing Protocol Eigrp



Isis Vs Ospf
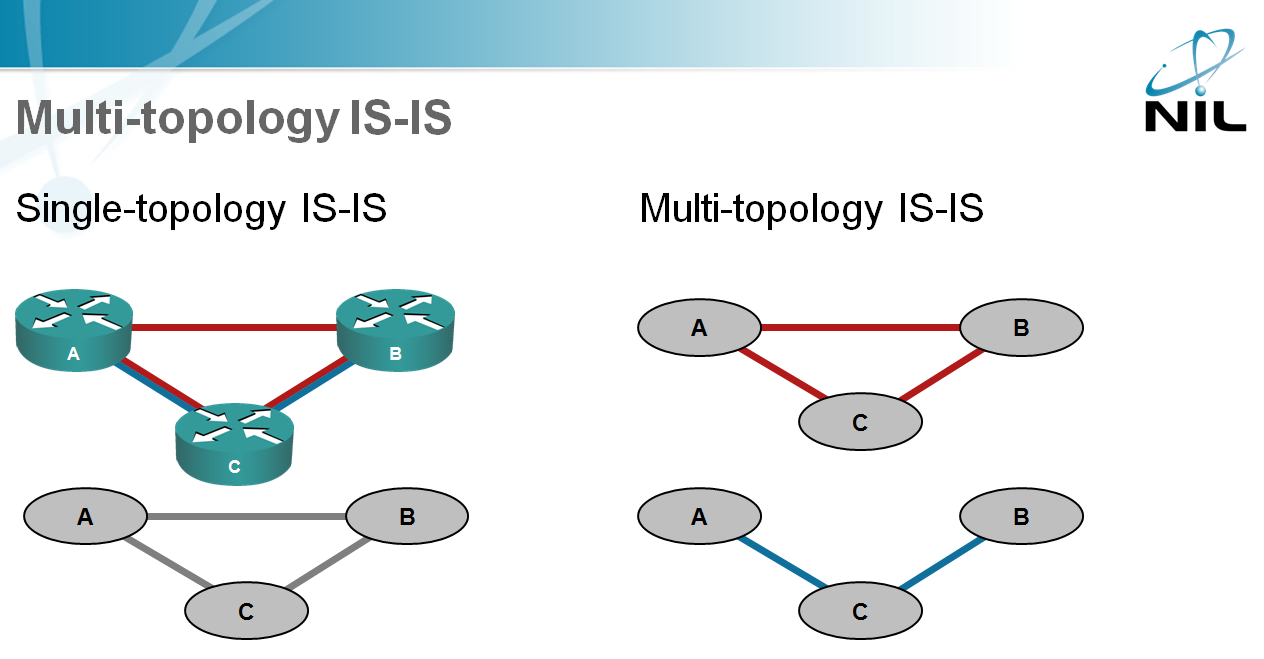



Multi Topology Is Is Ipspace Net Blog
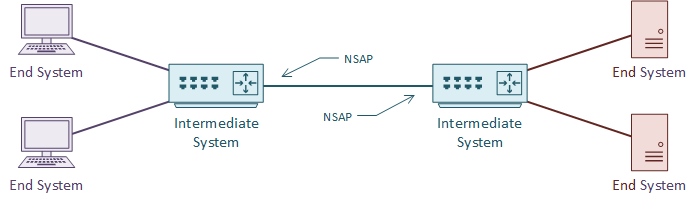



Introduction To Is Is Network Direction



Is Is Link State Packets Is Is Network Design Solutions Networking Technology



Routing Tables Part 2




How Does Is Is Routing Protocol Work Step By Step Explaination
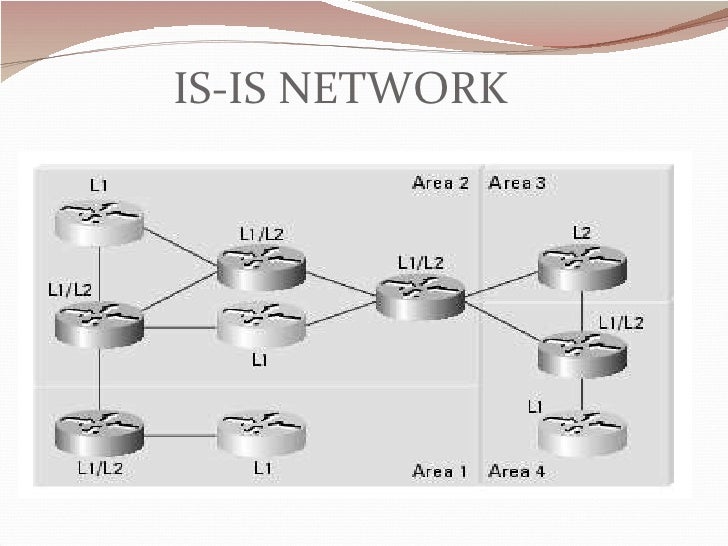



Is Is Routing Protocol
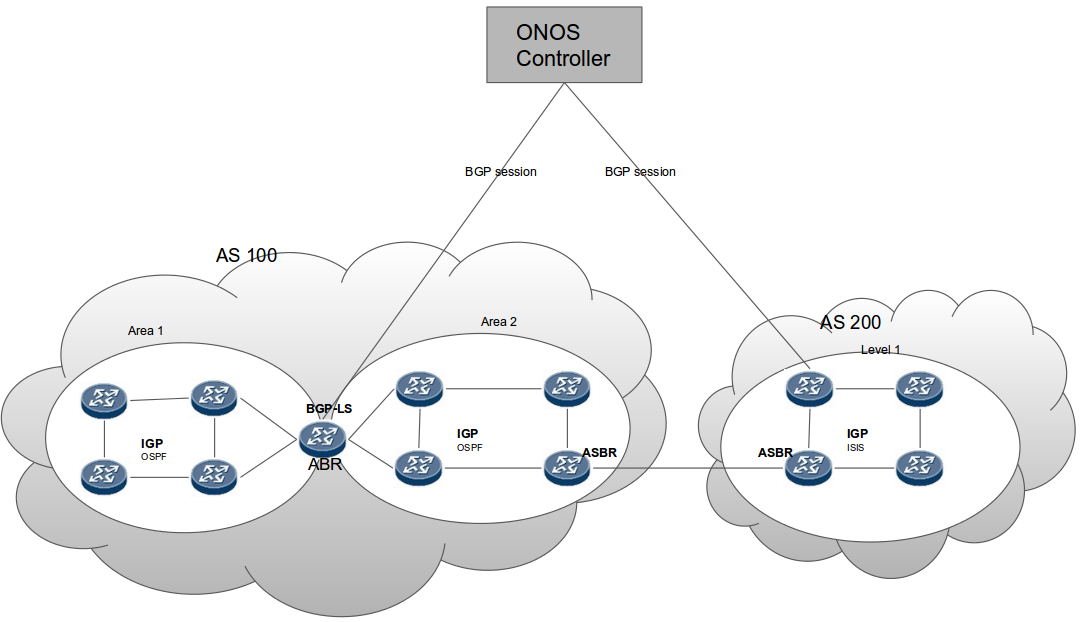



Bgp Protocol With Link State Distribution Onos Wiki
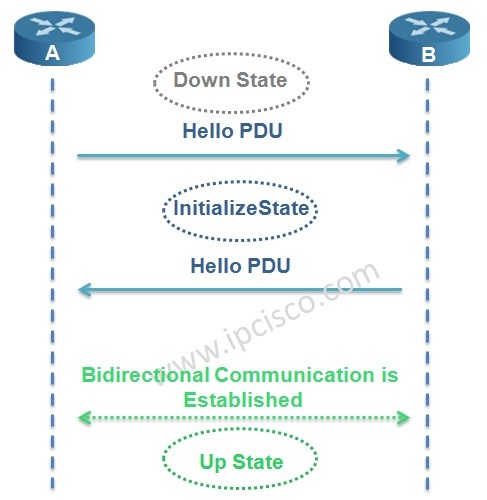



Is Is Adjacency Ipcisco




Is Is Control Messages Me60 V800r010c10spc500 Feature Description Wan Access 01 Huawei



1




Ospf And Is Is Differences And Similarties




Is Is Routing Protocol Study Notes Part 1 Network Walks Academy
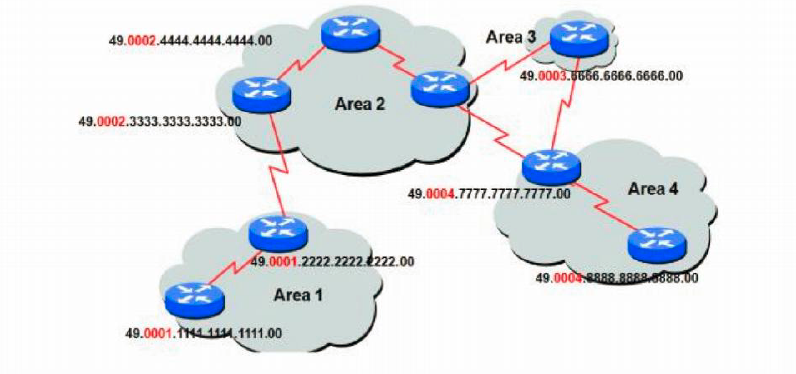



Intermediate System Intermediate System Is Is Protocol Octa Networks



Types Of Routing Protocols The Ultimate Guide The Essentials
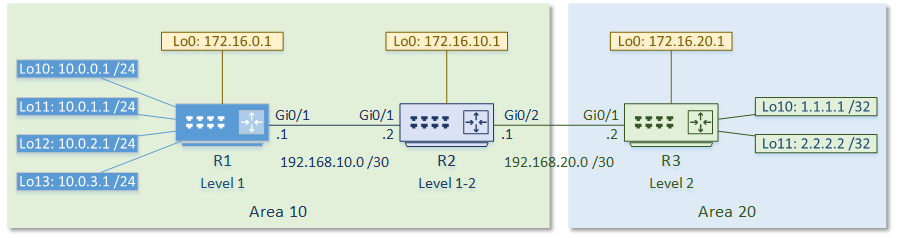



Introduction To Is Is Network Direction




Is Is Protocol Introduction




Configuring Is Is Protocol Overview Of Osi Protocols And Is Is Routing Cisco Press



Osi Routing




Isis Protocol Overview Youtube



Prezentaciya Na Temu C 06 Cisco Systems Inc All Rights Reserved Bsci V The Is Is Protocol Introducing Is Is And Integrated Is Is Routing Skachat Besplatno I Bez Registracii



Chapter 6 Routing Fundamentals



Isis Training And Junos Configuration Inetzero Inetzero
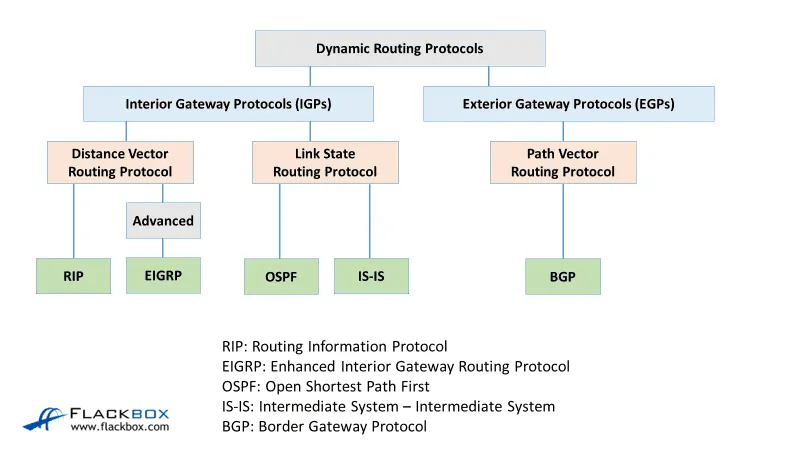



Cisco Routing Protocol Types Tutorial Flackbox
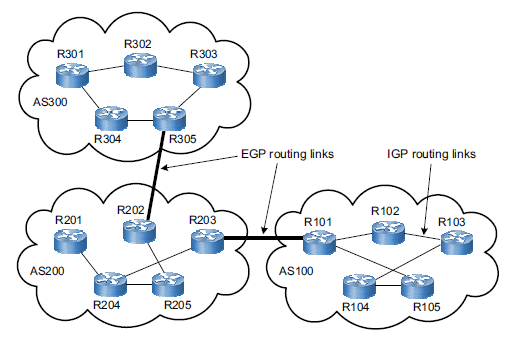



Is Is Terms And Concepts



0 件のコメント:
コメントを投稿